Saturday, December 25, 2010
Free Hosting
Sebelum menggunakan layanan free web hosting tersebut anda harus tahu dulu tentang ns atau name server. Name server ini dimiliki oleh web hosting, baik yang free atau yang berbayar. Name server ini harus dihubungkan dengan domain name anda. Biasaya dalam Cpanel domain name anda terdapat option untuk mengubah name server ini. Isilah name server (ns) dengan name server web hosting anda. Sebagai contoh jika anda menggunakan 000webhost.com sebagai web hosting anda, maka name server mereka adalah dns1.000webhost.com dan dns2.000webhost.com. Baca disini selengkapnya. Setiap pengubahan seting ns diperlukan waktu sampai maksimal 48 jam agar perubahan tersebut bisa dirasakan. Artinya internet memerlukan waktu sampai 48 jam untuk mengupdate seting website anda. Jika anda mengubah pada saat ini, mungkin saja web anda masih bisa diakses, karena internet belum mengupdate seting anda. Jika tidak bisa diakses, ya ditunggu saja.
Untuk free web hosting, ada beberapa penyedia free web hosting yang memberikan name servernya, jika mereka memberikan informasi tentang name servernya, maka free webhosting tersebut bisa digunakan untuk domian anda sendiri, maksudnya anda bisa membeli domain name dan menggunakan free web hosting tersebut sebagai hosting anda. Jagoan saya kali ini adalah 000webhost.com yang memberikan hosting gratis dan profesional. Tetapi ada juga yang tidak memberikan informasi tentang name servernya.
Ada langkah-langkah (harus urut) yang harus dijalani untuk mendapatkan free domain name dan free web hosting. Pertama anda harus mendaftarkan domain name dulu, baik free domain name maupun yang berbayar, setelah mendapatkannya, baru cari web hosting. Gunakan domain anda tersebut untuk mendapatkan web hosting. Pihak web hosting akan men-seting agar hosting pesanan anda mengarah ke domain anda. Setelah itu biasanya pihak web hosting akan memberitahu alamat name server mereka. Jika tidak tanyakan langsung kepada supportnya. Setelah mendapatkan alamat name servernya, setting option (di Cpanel domain anda) name server domain anda dengan name server web hosting yang baru saja di berikan tadi.
Dengan free hosting dan free domain anda bisa berbuat banyak, misalkan menginstall wordpress, membangun situs iklan baris menggunkan wordpress dan membangun aplikasi web dengan AJAX. And more..
Free domain name dan free web hosting adalah layanan gratis, anda tidak mengeluarkan uang sepeserpun untuk mendapatkan semua itu. Anda harus mematuhi TOS (Term of Service) yang mereka berikan, sekali anda dinilai melanggar, maka anda akan di kenai sanksi, misalkan dibanned. Dan bisa saja anda akan kehilangan data.
Friday, February 5, 2010
TOOLBARS
Most programs you use will have a title bar, menu bar, and toolbars along the top, as in the example shown in Figure 1. The exact appearance of these things will vary from one program to the next. But their purpose is generally the same in all programs:
• Title bar: Shows the name of the document and program, lets you move and size the entire program window.
• Menu bar: Provides access to all the tools that the program offers.
• Toolbar(s): Provide one-click access to all the commonly used tools on the menu bar.
Each little picture on the toolbar is a toolbar button. Some toolbar buttons show their names as a label. For example, the Back and Search toolbar buttons in Figure 2 above are both labeled. The rest of the toolbar buttons in that example have no labels. In most programs, you can point to (rest the mouse pointer on) a toolbar button to see the button's name, as in the example shown in Figure 2.
In most programs, toolbars are optional, and you can choose which ones you do and don't want to see. In most programs, options for showing and hiding toolbars are accessible from that program's View menu. Figure 3 shows an example where I've clicked on View in the program's menu bar and chosen the Toolbars option. The names on the submenu to the right show the names of toolbars available to me in that sample program (Standard Buttons, Address Bar, Links, and Google).
Notice in the example shown in Figure 3 that two toolbars have check marks next to their names. The checkmark means that those two toolbars are currently "on", and thereby visible in the program window. The toolbars names with no check mark next to them are currently "off", and therefore aren't visible in the program window.
Each option on the submenu is a toggle, meaning if you click on an option, you switch it to its opposite state. For example, if I were to click on the Standard Buttons option in Figure 3, that would turn the Standard Buttons toolbar off, making it invisible. Choosing View > Toolbars > Standard Buttons from the same menu bar again would turn the Standard Buttons toolbar back on, thereby making it visible again.
Arranging Toolbars
Many programs have toolbars that you can size and position within the program window. You can also lock the toolbars, to avoid accidentally rearranging the them after you get them arranged the way you like. You can tell if the toolbars are currently locked or unlocked just by looking at them. If the toolbars are locked, you'll see a handle (also called a dragging handle or sizing handle) to the left of each toolbar. The handle is just a vertical column of dots, as in the top half of Figure 4. When the toolbars are locked, the handles aren't visible, as in the bottom half of that same figure.
Figure 4: Unlocked toolbars show dragging handles
• If the toolbars are currently unlocked, choose View > Toolbars > Lock the Toolbars to lock the toolbars.
• If the toolbars are currently locked, choose View > Toolbars > Lock the Toolbars to unlock the toolbars.
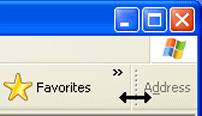
When the toolbars are unlocked, it's easy to accidentally rearrange them, as in the example shown in Figure 5 where the Address toolbar is now squished off at the right side of the Standard Toolbars button.
To get the Address bar back to its own row, you first need to make sure you can see the sizing handle. Notice that when you point to (rest the tip of the mouse pointer on) the sizing handle, the mouse pointer turns to a two headed arrow, as in the example shown in Figure 6.
Whenever the mouse pointer changes to arrows like that, it means "drag to move or size". If you drag that handle straight down a little, and over to the left, you can put the Address bar on its own row, as in Figure 7.
When you have the toolbars arranged the way you like in a program, you can lock them. That way you won't accidentally move them while you're whipping around the screen with your mouse. Note that you can show or hide toolbars whether the toolbars are locked or unlocked. But if you want to move or size the toolbars, you need to unlock them first.
SOFTWARE
Software is the general term for information that's recorded onto some kind of medium. For example, when you go to the video store and rent or buy a tape or DVD, what you're really getting is the software that's stored on that tape or disk. Your VCR or DVD player are hardware devices that are capable of reading the software from a tape or disk and projecting it onto your TV screen, in the form of a movie.
Your computer is a hardware device that reads software too. Most of the software on your computer comes in the form of programs. A program consists of "instructions" that tell the computer what to do, how to behave. Just as there are thousands of albums you can buy on CD for your stereo, and thousands of movies you can buy to play on your VCR or DVD player, there are thousands of programs that you can buy to run on your computer.
When you buy a computer, you don't automatically get every program produced by every software company in the world. You usually get some programs. For example, when you buy a computer it will probably have an operating system (like Windows XP) already installed on it.
If you do purchase a specific program, it would be to perform some specific task. For example, you might use a graphics program to touch up photos, or you might use a word processing program to write text. You're using your Web browser program right now to read this text (assuming you're not reading a printed copy on paper). Just as there are umpteen different brands of toothpaste, there are umpteen different brands of word processing programs, graphics programs, and Web browsers.
For example, all graphics programs are designed to help you work with pictures. But there are many brands of graphics programs out there, including Adobe Photoshop, Jasc Paint Shop Pro. Adobe Illustrator, Arcsoft PhotoStudio, Corel Draw, ULead PhotoImpact, PrintShop Photo, and Macromedia Freehand, just to name a few. As to Web browsers, popular brands include Microsoft Internet Explorer, MSN Explorer, Netscape Navigator, America Online, and a few others.
When you purchase a program, you get the program stored on a CD as in the example shown at left. You may not have seen any boxes containing software when you bought your computer. That's because the software that came with your computer has been pre-installed onto your computer's hard disk for you. You don't need to use the CD to run a program that's already installed on your computer. You only need to keep the CDs as backups, in case something goes wrong with your hard disk and you need to re-install the programs.
What Programs Do I Have?
Perhaps you're wondering what programs are installed on your computer. Usually when you buy a computer, they tell you what programs you're getting with it. So if you were to go back to the original ad from which you bought your computer, you'd probably find the names of programs you already have listed there. Though there's no need to do that, because every program that's currently installed on your computer is listed in your All Programs menu (assuming you're using Windows XP).
When you first open the Start menu, the left column lists programs you've used the most recently (Figure 1). If your computer is brand new, then the programs listed there will just be some examples.
That little list of program icons and names on the left side of the menu doesn't represent all the programs that are currently installed on your computer. Not by a long shot. The All Programs option on the Start menu provides access to all your installed programs. When you first click on (or just point to) the All Programs option, the All Programs menu that appears (Figure 2) will show icons and name of program groups, as well as some programs.
It's easy to tell the difference between a program and a program group. The program groups all have the same icon, and all have a right-pointing triangle (4) at their right side. When you click on, or point to, a program group, icons and names of programs within that group appear on a submenu. The submenu will contain programs within that group, and perhaps some more program groups. For example, Figure 3 shows the result of clicking on the Accessories program group in the All Programs menu. The submenu that opens contains more program groups, and specific programs you can run.
Your Start menu won't look exactly like the one shown in the figures, because different computers have different programs installed. (Just like different people who own CD players own different CDs).
Running Programs
When you click on the icon for a program, the program opens. Which means the program appears on the screen, so you can use it. Each program will appear in its own program window on the Windows desktop. For example, in Figure 4 the photograph in the background is the Windows desktop. Floating about on top of that desktop are four different program, each in its own separate program window.
Elements of Program Windows
While not two programs are exactly alike, most program windows contain certain similar elements. Stretched across the top of the program window is the title bar, which usually shows the name of the program that's inside the program window. Beneath the title bar is the menu bar, which gives you access to the tools and capabilities of that specific program. Many programs have a toolbar under their menu bar. The toolbar provides quick one-click access to frequently-used commands in the menu bar. The status bar at the bottom of a program provides general information. Figure 5 shows, in animated form, the title bar, menu bar, toolbar, and status bar of several different sample programs.
Figure 5
What's Available?
If you ever want to get an idea of the different types of programs that are available for your Windows XP computer, just go to any large computer store, or even a large office supply store like Staples, and take a look at the computer software. Or, you could even go into a large bookstore and look at the computer books sections. There will probably be a ton of books -- all for different programs like Microsoft Word, Microsoft Excel, WordPerfect, and of course Windows XP.
If you're comfortable using the World Wide Web, you can check our programs that are available by visiting the Windows Catalog Web site at:
www.WindowsCatalog.com
When you get to the Windows Catalog home page, click on the Software tab near the top of the page. Then click on the various categories of programs at the left side of the page (Figure 6). Each will display a submenu if types of programs within that category. You can click on any subcategory name to view programs within that subcategory. Or you can just click on any category name in that left column.
Keep in mind that there's a huge difference between viewing programs on your own Start menu, and viewing programs at the Windows Product Catalog Web site or a computer store. Programs on your Start menu are already installed on your computer and ready for you to use. Programs in a store or presented on the Windows Catalog Web site are programs you could buy and install on your computer.
Remember, software is to a computer as music is to a CD player, or as a movie is to a VCR. There are thousands of programs available for your PC, and no two people have exactly the same programs on their computers. The programs that are installed on your computer can all be found, and started from, the All Programs menu (or some program group that's accessible from All Programs menu). Windows XP, the topic of this course, is software too.
VIRUS
Unlike a virus that a human or animal catches, which was created by Mother Nature, a computer virus is a program, written by a human being, to do bad things to your computer. (Or, at the very least, open up a "hole" in your Internet connection through which advertisers can send annoying pop-up ads).
These programs are called viruses (or worms) only because they behave like viruses found in nature. When you (as a human) get a virus, you get sick because the virus replicates itself (makes copies of itself) and starts spreading throughout your body. A computer virus is much the same. It's a program that's able to make copies of itself, and spread itself throughout files in your computer.

Most viruses can also spread themselves by e-mailing themselves to people in your address book. You won't be aware that you're sending out these viruses, even if you're sitting at your computer while it's happening. Your friends will just start receiving e-mails from you with the virus attached. Likewise, when a friend of yours receives a file, it's likely that the virus will e-mail itself from their computer to yours.
As a rule, a virus will be sent as an attachment to an e-mail message. In some cases, the return address on the e-mail message will be your friend's e-mail address. In other cases, it will be some other bogus return e-mail message. For example, Figure 1 below shows my e-mail Inbox. I can tell, without even opening these e-mails, that the e-mails are not really from support@microsoft.com, and that all the attachments are all viruses.
Figure 1
All the messages with support@microsoft.com are suspicious to me for several reasons. For one, I haven't written to support@microsoft.com lately, so I'm not expecting any e-mail from them. For another, the body of the message doesn't really tell me what's in the attached file. When a virus sends itself to another computer, it tends to put only a tiny amount of text, or no text at all, into the body of the e-mail message. Another reason I'd be suspicious of the attachments in Figure 1 is that I know that Microsoft wouldn't send me (or anyone else) an attachment. It's just bad policy to be sending out e-mail messages (with or without attachments) to people at random.
If I were to open one of the attachments from Figure 1, my computer would then be infected with the virus. (I don't have to worry about this though because my e-Mail client, Microsoft Outlook, won't allow me to open any of these). Once my computer is infected, the virus would try to send copies of itself out to other people in my address book. (It would fail there too, though, because Outlook would warn me when a virus is trying to send itself).
Anyway, the question becomes "How does the average person tell the difference between a legitimate e-mail attachment, and a virus, just by looking?" You really can't. But there are steps you can take to protect yourself from viruses. For starters, never open an e-mail attachment unless:
1. You know who it's from
2. You were expecting the attachment
3. You know what's in the attachment
Remember, a friend's computer can send you a virus without your friend even knowing it. So don't assume that just because it's from a friend, it's safe. If in doubt, write your friend and find out if they sent you an e-mail with a legitimate attachment. Also, there's no guarantee that the return address on the e-mail is the real return address. So don't rely entirely on the sender's e-mail address as a means of determining whether or not an e-mail attachment is a virus.
E-mail messages aren't the only way viruses are spread. Many programs that you can download for free will be infected as well. Any time you get an e-mail message offering some cool, cute, free program you can download just by "clicking", be suspicious. Be very suspicious. In particular, be very leery of "cute". In the computer world, "cute" most definitely doesn't equate to "harmless".
Be aware, though, that not all downloads are dangerous. Downloads from legitimate software companies like Microsoft or online services like www.tucows.com should be perfectly safe.
Finally, you should purchase, install, and learn to use anti-virus software. If your computer came with anti-virus software, then you just have to learn to use it. You should be able to find some instructions in with the rest of the printed material that came with your computer.
DOWNLOAD
To download something means to copy it from some other computer's hard disk to your own computer's hard disk, as illustrated in Figure 1. (By the way, if you're viewing a printed copy of this lesson, be aware that the copy on the screen is animated to show the concept). After you download something, you can access the copy that's stored on your hard disk at any time, even when you're offline.
Figure 1
The term upload means the opposite of download -- to copy something from your own computer's hard disk to some other computer on the Internet. If you can envision the Internet as a "cloud up in the sky", then it's easy to keep track of the difference between the terms upload and download.
Since you already have an Internet connection, you probably has an e-mail (electronic mail) account too. If so, then you have an e-mail address, the address people use when they want to send you an e-mail message. All e-mail addresses look something like someone@somewhere.xxx (unlike a Web site's URL, which looks something like www.somplace.xxx) Before you can use e-mail, you need to know your own e-mail address, and the password required to retrieve e-mail messages that other people have sent you. Only your Internet Service Provider can give you that information.
To send and receive e-mail, you use a program known as an e-mail client. There are lots of different ISPs in the world, and lots of different e-mail clients. If you ever need to ask someone a question about using your e-mail, you won't be able to get an answer until the person you're asking knows what program you're using as your e-mail client. In some cases, they'll be able to guess just by knowing the domain name of your e-mail service. The domain name is the part that comes after the @ in your e-mail address. For example, if you e-mail address is wanda@aol.com, then the domain name is aol.com. If your e-mail address is harry@yahoo.com, then the domain name is yahoo.com.
But knowing the domain name isn't always enough, because many ISPs let you choose what program you use for e-mail. For example, you might have an e-mail address like wilma@comcast.net. If so, you might be using a program named Outlook Express as your e-mail client, or you might be using Microsoft Outlook 2003 as your e-mail client. In short, getting a simple answer to a simple e-mail question isn't always so easy.
Here we'll take a look at some different types of e-mail, and hopefully you'll be able to learn a bit about the e-mail system you're using.
America Online
If you have an Internet account with America Online (AOL), and your e-mail address ends in @aol.com. then you probably use America Online (Figure 1) for e-mail.

Figure 1
MSN and Hotmail
If you have an Internet account with the Microsoft Network (MSN), or if your e-mail address ends in @msn.com or @hotmail.com, then you probably use MSN Explorer (Figure 2) as your e-mail client.

Figure 2
Some of you might use Netscape Navigator as your e-mail client. This is almost certain true if your e-mail address end in @netscape.com. Though Netscape Navigator works with other e-mail domains as well. Figure 3 shows the e-mail client portion of Netscape Navigator.

Figure 3
Many people use Microsoft Outlook Express as their e-mail client. That's because Outlook Express comes free with every copy of Microsoft Windows, and it works with many (though not all) e-mail domains. Figure 4 shows what Outlook Express looks like on the screen when its open.

Figure 4
Microsoft Outlook
Microsoft Office comes with yet another e-mail client called Microsoft Outlook. Outlook is Outlook Express's "big brother". It has all the same e-mail capabilities as Outlook Express, but includes lots of other things like a calendar, and a fancy address book. Figure 5 shows how Microsoft Outlook appears on the screen when open.

Figure 5
Yahoo
Yahoo is yet another popular e-mail service. Yahoo doesn't require any special e-mail client. Instead, you just use your Web browser to do e-mail with Yahoo. Figure 6 shows how Yahoo e-mail looks on the screen.

Figure 6
If you're really lost with e-mail, or just have a question on one specific aspect of your e-mail, such as using attachments, your best resource will be your ISP. If you can at least get to the place where you send and receive e-mail messages, look around that page for a Help link, and click on that. Then look around for a specific word or phrase that's relevant to your problem, such as attach or attachments. Hopefully you'll be able to get specific instructions for your e-mail client. Those specific instructions will be more useful to you than general instructions that apply to all e-mail clients and all domains.
PC PORTS
There are lots of external devices that you can connect to your computer. All external devices connect to the computer’s system unit via cables and ports (where a "port" is the slot into which you plug a cable). Unless you’re using a portable computer, you probably have several external devices attached to your computer already, including a mouse, keyboard, monitor, microphone, and speakers, as in Figure 1.
 Figure 1: Computer (system unit) and attached external devices.
Figure 1: Computer (system unit) and attached external devices.Whatever external devices you have, they're all connected to the system unit (where the actual "computing" takes place) via cables. Each cable plugs into a specific port on the system unit. The ports are usually on the back of the system unit. But they can be on front or side as well.
Everything has a name, even (believe it or not) those little plugs on the back of your computer. Figure 2 shows examples of some ports. But your computer's ports won't necessarily be the same.
Figure 2: Examples of ports
USB and FireWire Ports
Of all the ports on a computer, USB and IEEE 1394 (a.k.a. FireWire) get all the hype. There are several reasons for this: Both are new technologies, both provide "hot-pluggable" connectivity, both provide very high-speed data transfers. The hot-pluggable part means you can just plug in some device, like a digital camera or video camera, and start using it right away. (The older ports would all require you to shut down the computer, plug in the device, restart the computer, then install the device.). In short, both USB and FireWire are a lot more convenient than the older ports that preceded them.
So what are the differences? In a nutshell, USB (Universal Serial Bus) was created as a general-purpose high-speed connection to the computer. It's high speed makes it ideal for connecting digital cameras to the computer. But it's good for lots of other devices too, like a Web cam, broadband modem, whatever.
IEEE (Institute of Electrical and Electronics Engineers) 1394, also known commercially as FireWire, is a faster connection than USB, but not as widely used. In consumer electronics, it's mostly digital video cameras that connect through a FireWire port. There are also some high-speed external disk drives and networking components that can use that port. Because FireWire devices are relatively rare, FireWire ports are also rare. Just about any computer you buy will have at least two USB ports. But it's unlikely you'd get a FireWire port if you didn't specifically order it with your PC. (Of course, you can always add a FireWire port at any time. No problem there).
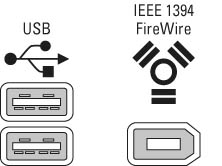
As though to confuse matters even more, the plugs for USB and FireWire look very much alike. Each port type, however, has its own little logo, as shown in Figure 3. As you can see just by looking at the plugs, the plug for USB won't go into a FireWire port, or vice-versa.
Figure 3: USB and FireWire ports (computer side of cable)
Note that Figure 3 shows how USB and FireWire ports as they look on a computer. On the device you're connecting (for example), the plug might be an entirely different size and shape. Check the manual that came with your device if you can't find the right plug
PERSONAL KOMPUTER
Your PC (Personal Computer) is a system, consisting of many components. Some of those components, like Windows XP, and all your other programs, are software. The stuff you can actually see and touch, and would likely break if you threw it out a fifth-story window, is hardware.
 Not everybody has exactly the same hardware. But those of you who have a desktop system, like the example shown in Figure 1, probably have most of the components shown in that same figure. Those of you with notebook computers probably have most of the same components. Only in your case the components are all integrated into a single book-sized portable unit.
Not everybody has exactly the same hardware. But those of you who have a desktop system, like the example shown in Figure 1, probably have most of the components shown in that same figure. Those of you with notebook computers probably have most of the same components. Only in your case the components are all integrated into a single book-sized portable unit.The system unit is the actual computer; everything else is called a peripheral device. Your computer's system unit probably has at least one floppy disk drive, and one CD or DVD drive, into which you can insert floppy disks and CDs. There's another disk drive, called the hard disk inside the system unit, as shown in Figure 2. You can't remove that disk, or even see it. But it's there. And everything that's currently "in your computer" is actually stored on that hard disk. (We know this because there is no place else inside the computer where you can store information!).
 The floppy drive and CD drive are often referred to as drives with removable media or removable drives for short, because you can remove whatever disk is currently in the drive, and replace it with another. Your computer's hard disk can store as much information as tens of thousands of floppy disks, so don't worry about running out of space on your hard disk any time soon. As a rule, you want to store everything you create or download on your hard disk. Use the floppy disks and CDs to send copies of files through the mail, or to make backup copies of important items.
The floppy drive and CD drive are often referred to as drives with removable media or removable drives for short, because you can remove whatever disk is currently in the drive, and replace it with another. Your computer's hard disk can store as much information as tens of thousands of floppy disks, so don't worry about running out of space on your hard disk any time soon. As a rule, you want to store everything you create or download on your hard disk. Use the floppy disks and CDs to send copies of files through the mail, or to make backup copies of important items.Random Access Memory (RAM)
There's too much "stuff" on your computer's hard disk to use it all at the same time. During the average session sitting at the computer, you'll probably use only a small amount of all that's available. The stuff you're working with at any given moment is stored in random access memory (often abbreviated RAM, and often called simply "memory"). The advantage using RAM to store whatever you're working on at the moment is that RAM is very fast. Much faster than any disk. For you, "fast" translates to less time waiting and more time being productive.
So if RAM is so fast, why not put everything in it? Why have a hard disk at all? The answer to that lies in the fact that RAM is volatile. As soon as the computer is shut off, whether intentionally or by an accidental power outage, every thing in RAM disappears, just as quickly as a light bulb goes out when the plug is pulled. So you don't want to rely on RAM to hold everything. A disk, on the other hand, holds its information whether the power is on or off.
The Hard Disk
All of the information that's "in your computer", so to speak, is stored on your computer's hard disk. You never see that actual hard disk because it's sealed inside a special housing and needs to stay that way. Unlike RAM, which is volatile, the hard disk can hold information forever -- with or without electricity. Most modern hard disks have tens of billions of bytes of storage space on them. Which, in English, means that you can create, save, and download files for months or years without using up all the storage space it provides.
In the unlikely event that you do manage to fill up your hard disk, Windows will start showing a little message on the screen that reads "You are running low on disk space" well in advance of any problems. In fact, if that message appears, it won't until you're down to about 800 MB of free space. And 800 MB of empty space is equal to about 600 blank floppy disks. That's still plenty of room!
The Mouse
Obviously you know how to use your mouse, since you must have used it to get here. But let's take a look at the facts and buzzwords anyway. Your mouse probably has at least two buttons on it. The button on the left is called the primary mouse button, the button on the right is called the secondary mouse button or just the right mouse button. I'll just refer to them as the left and right mouse buttons. Many mice have a small wheel between the two mouse buttons, as illustrated in Figure 3.

The idea is to rest your hand comfortably on the mouse, with your index finger touching (but not pressing on) the left mouse button. Then, as you move the mouse, the mouse pointer (the little arrow on the screen) moves in the same direction. When moving the mouse, try to keep the buttons aimed toward the monitor -- don't "twist" the mouse as that just makes it all the harder to control the position of the mouse pointer.
If you find yourself reaching too far to get the mouse pointer where you want it to be on the screen, just pick up the mouse, move it to where it's comfortable to hold it, and place it back down on the mousepad or desk. The buzzwords that describe how you use the mouse are as follows:
Point: To point to an item means to move the mouse pointer so that it's touching the item.
Click: Point to the item, then tap (press and release) the left mouse button.
Double-click: Point to the item, and tap the left mouse button twice in rapid succession - click-click as fast as you can.
Right-click: Point to the item, then tap the mouse button on the right.
Drag: Point to an item, then hold down the left mouse button as you move the mouse. To drop the item, release the left mouse button.
Right-drag: Point to an item, then hold down the right mouse button as you move the mouse. To drop the item, release the right mouse button.
The Keyboard
Like the mouse, the keyboard is a means of interacting with your computer. You really only need to use the keyboard when you're typing text. Most of the keys on the keyboard are laid out like the keys on a typewriter. But there are some special keys like Esc (Escape), Ctrl (Control), and Alt (Alternate). There are also some keys across the top of the keyboard labeled F1, F2, F3, and so forth. Those are called the function keys, and the exact role they play depends on which program you happen to be using at the moment.
Most keyboards also have a numeric keypad with the keys laid out like the keys on a typical adding machine. If you're accustomed to using an adding machine, you might want to use the numeric keypad, rather than the numbers across the top of the keyboard, to type numbers. It doesn't really matter which keys you use. The numeric keypad is just there as a convenience to people who are accustomed to adding machines.
 Most keyboards also contain a set of navigation keys. You can use the navigation keys to move around around through text on the screen. The navigation keys won't move the mouse pointer. Only the mouse moves the mouse pointer.
Most keyboards also contain a set of navigation keys. You can use the navigation keys to move around around through text on the screen. The navigation keys won't move the mouse pointer. Only the mouse moves the mouse pointer.On smaller keyboards where space is limited, such as on a notebook computer, the navigation keys and numeric keypad might be one in the same. There will be a Num Lock key on the keypad. When the Num Lock key is "on", the numeric keypad keys type numbers. When the Num Lock key is "off", the navigation keys come into play. The Num Lock key acts as a toggle. Which is to say, when you tap it, it switches to the opposite state. For example, if Num Lock is on, tapping that key turns it off. If Num Lock is off, tapping that key turns Num Lock on.
Combination Keystrokes (Shortcut keys)
Those mysterious Ctrl and Alt keys are often used in combination with other keys to perform some task. We often refer to these combination keystrokes as shortcut keys, because they provide an alternative to using the mouse to select menu options in programs. Shortcut keys are always expressed as:
key1+key2
where the idea is to hold down key1, tap key2, then release key1. For example, to press Ctrl+Esc hold down the Ctrl key (usually with your pinkie), tap the Esc key, then release the Ctrl key. To press Alt+F you hold down the Alt key, tap the letter F, then release the Alt key.
Thursday, February 4, 2010
Laptop Data Recovery
Laptop Data Recovery - Recovering Laptop Hard Drive Files With A USB Shell
| The worst thing that can happen to most laptop users, aside from the loss of the whole laptop, is hard drive failure. The hard drive holds all of your data, files, and all your e-mails and contacts if you use Outlook, Eudora, or any other non-portal based e-mail. But I'm sure many more laptops have gone to the recycling facility with live hard drives than dead hard drives. If you have any files you value on your hard drive that aren't backed up, you should invest $10 or $15 in a USB shell and attempt to recover the data. Hard drive data recovery is thought to be an arcane art, requiring expensive equipment and a high level of technical skill, but all of that only comes into play if the onboard electronics or the motor have failed. In that case, the drive platters are removed from the metal case in a special clean room, and the data is recovered by reading it off on a universal reader. |  |
 | Most laptop owners are still very foggy as to where their data resides and consider the whole lower part of the laptop (everything except the screen) to be part and parcel with the hard drive. In reality, laptop hard drive are 2.5" wide, about 4" long and about a quarter inch thick. They weigh a couple of ounces, and can normally be accessed by removing a single screw from the laptop, as shown above.You should always unplug the laptop and remove the battery before attempting to do any repair work. I'll admit I left the battery in here, because I knew it had been stone dead for some six months or more, since the AC adapter died. After removing the single screw, you can see the 2.5" laptop hard drive installed in its cage. This hard drive is an IBM Travelstar, perhaps the most common hard drive used in laptops the past couple years. Because it's an older laptop, there's no shock mounting for the drive, little rubber washers that have become a popular way to partially shield the hard drive from the vibrations that can cause head crashes, in which case you can't recovery the data with a million dollar lab.
|
| The series of pictures at the top of this page are for the older parallel ATA (PATA) drives, the newer SATA laptop hard drive is shown at the bottom of the page. The next step is to remove the whole cage from the laptop, which involves pulling back on the cage to free the drive's IDE interface from the laptop connector. You can see to the right that the drive cage is held from lifting by two metal tabs, and that the screw that held the plastic lid on the drive bay went all the way through and secured the cage in the laptop. That's all that held it together, one screw, and it's a typical arrangement. It turns out that removing the old hard drive from the cage, once it's out, is generally a bigger job than removing the cage from the laptop, because there are four screws involved and they are often overtightened and strip when you try to remove them. But it's not necessary to take it apart any further if all you want to to recover your old files. |  |
 | To the left, I'm holding the new USB 2.0 interface that came with the $14.95 Sabrent hard drive enclosure I bought from Amazon for $14.95. The interface is really all you need to gain access to the old hard drive, if it's healthy, and recover your data. The kit comes with software from Mac users as well as Windows based machines, but modern operating system versions don't even require the software. They'll just find the new USB hardware when it's plugged in, recognize that it's a hard drive, and allow you to recover your files as long as the file system types were compatible. I'm holding the interface card over the aluminum enclosure in which you could install the drive if you wanted to use it as a permanent external hard drive. |
| But when I started taking the screws out of the cage, three out of four fought me and the fourth stripped, despite the fact I was using a high quality screw driver. It would be easy to bend and break the remaining tab off to remove the cage, but why bother, when the only point of the job is to recover some old files? So I plugged the interface on (to the right), then set the whole thing down on my table with the new laptop and plugged it into the USB 2.0 port. You can see that the little green LED on the drive is lit and active, if you have good eyes and a better imagination. |  |
 | Immediately after plugging in the USB cable, Windows XP picked up on the drive, and asks what you want to do with it. Choose "View with Explorer" and you'll gain access to all of the old folders, drag them onto your new laptop hard drive, and your data recover job is complete. Well, after you burn the recovered files on a DVD it will be complete, and you won't face the worry again. If the LED doesn't light up, you could be plugging the USB into an old port that doesn't source the 500 mA required, or the interface could be bad out of the box, or the drive could really be dead. If you don't hear the drive spin up, you can try picking it up gently, a few inches over the table, and try rocking in slowly to see if you can feel the centripetal force of the disk spinning. |
| In the 2005/2006 time frame, laptops started changing over from the older IDE (PATA) hard drives to the newer SATA hard drive. The only difference, as far as the user is concerned, is that the SATA drives are faster and have a different connector. The drives are otherwise identical, and the SATA drives often cost less in the larger capacities as they are more common today. Since the SATA interface only requires a few wires (serial vs. parallel bus), ribbon cables aren't required and a more flexible and robust connection is possible. The picture to the right shows an SATA drive installed in the laptop bay, and thanks to the rubberized shock mounting around the bay and on the cover, it simply sits tightly in place - no screws required. I only needed to remove one screw to take this drive out and put it into an SATA USB enclosure, and that was the screw on the drive bay lid. |  |
 | Mounting the SATA drive on the circuit card for the external USB enclosure involves sliding the SATA edge connector into the circuit board connector and putting in a couple screws to hold it, if you're going to make the enclosure its permanent home. But don't make the mistake of thinking you're going to be able to boot your laptop from an external SATA hard drive, I haven't come across the laptop BIOS that can handle it yet. When the laptop BIOS gives you a "USB boot" option, it's the option to boot from a memory stick. Sabrent makes an SATA hard drive shell which costs $22.95 from Amazon. In any case, if your laptop is a brick and you need to recover your data, pulling out the hard drive and putting it in an external USB case is usually the easiest approach, providing that the hard drive itself isn't fried . |
 |
Fix Windows Errors - Runtime, Rundll32, DLL Files
Fix Windows Errors - Runtime, Rundll32, DLL Files
Diagnosing Windows Errors: Runtime Errors, Rundll32 exe, Kernel32, DLL, Win32 Errors, Blue Screen System Crashes, ActiveX, Application Errors and more...
A corrupt Windows registry can be the source of many troublesome PC problems. The Windows registry is an integral part of a computer's operating system. It consists of a database which stores configuration settings for all installed software, hardware, drivers, memory and system options on your computer. This also includes user preferences, settings and licence information. Attempting to manually edit the registry is extremely dangerous for your computer's operating system and you could create bigger problems than you have now. A Registry Cleaner is a specialized program designed to safely delete or repair erroneous registry settings.
If your registry is not properly maintained on an regular basis, then your computer system may begin experiencing system crashes, stalls or slower operating speeds. By placing a high priority on repairing registry problems and preventing system crashes you'll end up with greatly improved system stability and operating speeds.
There are a number of common PC errors that can be avoided with a properly maintained registry. If you're experiencing any of the following windows error messages then a good quality registry cleaner with the appropriate PC diagnostic features will be useful in diagnosing and repairing your system:
- Rundll32 exe
- Runtime Error
- Blue Screen
- Win32 Error
- Kernel32 DLL Error
- Rundll Error
- Dll Error
- Windows System32 Error
- Application Errors
- ActiveX Errors
- Startup Errors
One of the major problems impacting on the Windows Registry is redundant entries left over by uninstalled software and hidden adware, spyware and viruses. The Windows Add/Remove Programs utility and even official software uninstallers do not completely clean out your registry entries. If you have or had a spyware infection your anti-spyware tool might not completely remove all its registry entries. A registry cleaner is a tool that allows you to get rid of these troublesome and obsolete registry entries created by programs and drivers that were not properly uninstalled in the past. It does not require any technical expertise to use it so don't be concerned about any limitation in computer knowledge.
Some good reasons to clean your registry:
- you frequently install and uninstall software
- you uninstalled software that were never completely uninstalled
- you have spyware or adware programs that you can't uninstall
- you had previous spyware, adware or virus infections
- you have uninstalled hardware
- you have unused drivers on your system
With so many changes occurring over time through the normal use of your computer, your registry can become filled with errors and obsolete entries. Whenever you remove programs, it's highly probable that not all the components are completely removed from your hard drive or registry. If your registry is not properly cleaned of these obsolete entries and errors you'll be left with ongoing system problems as your computer attempts to process invalid instructions.
A good quality registry cleaner should also be able to detect:
- Missing file associations
- Missing startup programs
- Missing help files
- Missing system fonts
- Missing DLL files
- Invalid device drivers
- Invalid application paths
A good quality registry cleaner that we recommend for fixing and preventing many common PC problems is Regcure. It's very easy to use and consistantly finds registry errors that competing software miss. It's features include system restore points and scheduled scanning so you can set it to scan automatically.
RegCure features: 
- Easy to use interface
- Full registry backup
- Built in scheduler
- Startup manager
- Deletes empty registry Keys
- Compress or Defrag Registry
- COM/ActiveX scanning
- Removes duplicate files
- Checks invalid Class Keys
- Checks missing font files
- Checks DLL conflicts
- Checks invalid application paths
- Checks invalid shortcuts
- Checks invalid file associations